What is a TCP Data Flood Attack?
A TCP Data Flood attack is a type of Distributed Denial of Service (DDoS) attack where an attacker attempts to overwhelm a target server by sending a large volume of TCP packets containing junk data or simulated normal user data. The primary objective of this attack is to exhaust the server’s resources, disrupt regular traffic, and deny service to legitimate users.
TCP Data Flood Attack Mechanism
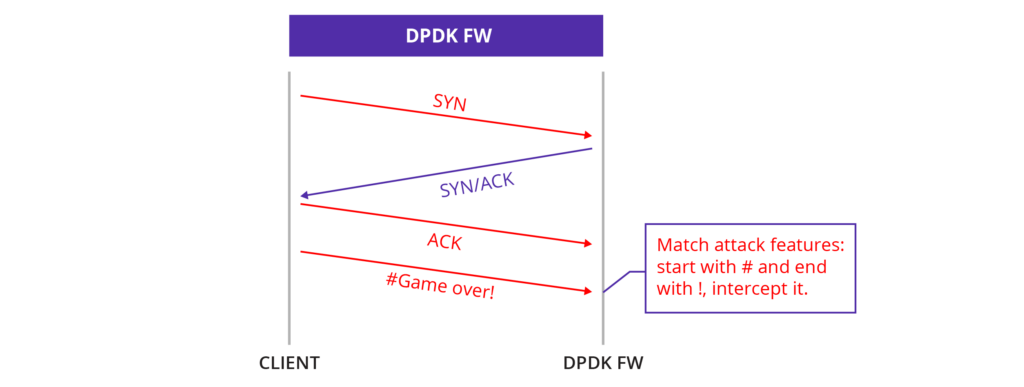
In a TCP Data Flood attack, the attacker first establishes a legitimate connection with the target server by completing the TCP three-way handshake. Once the connection is established, the attacker floods the server with an excessive amount of data packets. These packets may contain meaningless data or mimic normal user traffic patterns.
The server must process each incoming packet, consuming significant computational resources and network bandwidth. As the server struggles to handle the influx of data, its performance degrades, leading to slowdowns or complete service outages for legitimate users.
Unlike some other DDoS attacks that focus on connection establishment (such as SYN 플러드), TCP Data Flood attacks exploit fully established connections. This makes them particularly challenging to detect and mitigate, as the initial connection appears legitimate.
Protecting Against TCP Data Flood Attacks
Defending against TCP Data Flood attacks involves several strategies:
1. Matching Attack Characteristics: Implement systems that can identify and intercept traffic based on known attack patterns or signatures.
2. Resource Limiting: Set thresholds to restrict the number of new connections, concurrent connections, or bandwidth usage from individual IP addresses. Apply rate limiting or blacklisting to sources exceeding these thresholds.
3. TCP Watermarking: For client-type applications, modify the client to include a verification field (watermark) in the TCP data of normal business traffic. The DPDK firewall can then check this field and only allow packets with the correct watermark to pass through.
4. Advanced Intrusion Detection and Prevention Systems (IDPS): Deploy systems capable of identifying and blocking suspicious traffic patterns indicative of a TCP Data Flood attack.
5. Traffic Analysis and Anomaly Detection: Continuously monitor network traffic for unusual patterns or sudden spikes that may indicate an ongoing attack.
In summary, a TCP Data Flood attack exploits established connections to overwhelm servers with excessive data, leading to resource exhaustion and service disruption. Effective defense mechanisms, including traffic analysis, resource limiting, and TCP watermarking, are crucial to protect against these sophisticated and potentially damaging cyberattacks.