今日のデジタル世界では、インターネットは人々の日常生活やビジネス活動に欠かせないものとなっています。この広大で複雑なネットワーク エコシステムでは、IP アドレスはさまざまなネットワーク デバイスやサービスを接続および識別するための基本です。ただし、デバイスの IP アドレスを知るだけでは、ネットワーク内での役割と動作を完全に理解することはできません。IP アドレスをより深く理解し、より有効に活用するために、リバース DNS (rDNS) テクノロジは貴重な情報を提供し、IP アドレスに関する詳細を明らかにするのに役立ちます。
rDNS とは何ですか?
DNS とは異なり、rDNS は PTR レコードと CNAME レコードを照会して IP アドレスをドメイン名に変換するプロセスです。IP アドレスは複数のドメイン名に対応し、1 対多の関係を表します。対照的に、IP アドレスの逆引き検索では通常 0 個または 1 個のホスト名が返され、1 対 1 の関係を表します。逆引き DNS の一般的な用途は次のとおりです。
- 送信者の身元を確認する
rDNSは、スパムメールの防止や、 フィッシング攻撃サーバーから電子メールが送信されると、受信サーバーは送信サーバーの IP アドレスを確認し、rDNS クエリを実行してその IP アドレスに関連付けられたドメイン名を確認できます。rDNS レコードが送信サーバーの要求と一致する場合、これは送信サーバーの ID の検証として機能し、電子メールが正当である可能性が高まります。たとえば、AOL (America Online) では、AOL/AIM メールボックスに電子メールを送信するには、送信者のメール サーバーが逆引き可能である必要があります。一部の大規模ネットワーク プロバイダーでは、正しい逆引き DNS レコードを構成することも、インターネット サービスの信頼性と信頼性を確立する一環となっています。
- ネットワークのトラブルシューティングと追跡
ネットワーク管理とトラブルシューティングでは、要求元デバイスのドメイン名情報を知ることが非常に役立ちます。rDNS は、ネットワーク管理者がネットワーク トラフィック内の特定のホストを識別し、トラフィックのソースを理解するのに役立ち、問題を効果的に診断できるようにします。
- セキュリティポリシーとアクセス制御の実装
一部のネットワーク サービスとアプリケーションは、セキュリティ ポリシーやアクセス制御を実装するために逆ドメイン名に依存している場合があります。rDNS を通じて、サービスはアクセス要求の IP アドレスの背後にあるドメイン名をチェックして、アクセスを許可するか、特定のルールを適用するかを決定できます。たとえば、要求ヘッダーの User-Agent と IP の逆解決レコードを検証して無害なボットを識別し、要求が本物の SEO クローラーからのものであるかどうかを確認します。
逆DNSから地理的位置情報を取得する
実行中 ホスト 96.227.5.107 ターミナル利回り プール-96-227-5-107.phlapa.east.verizon.net。サブドメイン部分を示す .phlapa IPアドレスが米国ペンシルベニア州フィラデルフィアにあることが示唆されます。同様に、逆引き検索を実行すると、 63.153.137.40 結果的に 63-153-137-40.sxfl.qwest.net.サブドメイン部分 .sxfl. は、米国サウスダコタ州スーフォールズの略称です。ホスト名を調べることで、その地理的位置を推測することができ、rDNS レコードが IP 地理位置情報に追加の価値を提供できることがわかります。ただし、考慮すべき点は次のとおりです。
- IPv4 アドレス空間全体で逆解決できる IP アドレスはいくつありますか?
- 逆解決可能な IP アドレスの中に、地理的な位置情報を含む rDNS レコードはいくつ存在しますか?
論文「リバース DNS による IP ジオロケーション「、私たちはかなり妥当な解決策を見つけました。この論文では、rDNS から位置情報を抽出する機械学習アプローチを提案し、タスクを機械学習の問題として扱います。特定のホスト名に対して候補となる場所のリストを生成し、バイナリ分類器を使用して各ホスト名と候補となる場所のペアを分類し、どの候補となる場所が妥当であるかを判断します。最後に、残りの候補となる場所は信頼性に基づいてランク付けされ、人口数と相関します。この方法は、現在主流となっている IP Geo 商用データベースの精度を効果的に補完し、強化します。
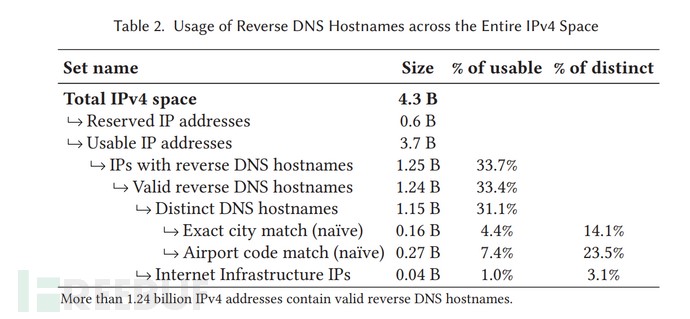
図1: IPv4アドレス空間におけるrDNSの分布
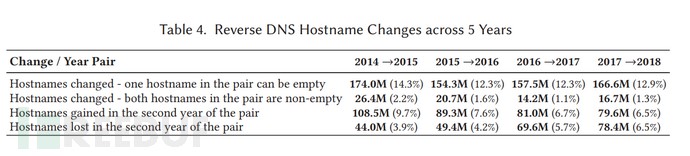
合計 43 億の IPv4 アドレス空間のうち、パブリック IP アドレスは約 25 億 6,800 万個あります。上のグラフは、12 億 5,000 万個の IPv4 アドレスに有効な rDNS があることを示しています。これらの 12 億 5,000 万個の IPv4 アドレスのうち、約 1 億 6,000 万個に正確な都市の一致が含まれ、2 億 7,000 万個に空港コードが含まれています。つまり、有効な逆 DNS レコード全体のうち、有用な地理的位置情報が含まれているのは約 12% のみです。これらのレコードの範囲は、完全な IP Geo データベースを単独で形成するには不十分ですが、既存の IP 地理位置情報の充実には貢献できます。さらに、この論文では 2014 年から 2018 年までの rDNS の変化を分析し、64.8% の rDNS 解決レコードは変更されておらず、逆 DNS レコードの数は毎年ゆっくりと増加していることを示しています。この事実は、現在約 12 億 8,600 万個である最新の rDNS データと一致しています。
図2: 2014年から2018年までのrDNSホスト名の変更
MaxMind、Neustar IP Intelligence、IP2Location などの企業が提供する商用 IP 地理位置情報データベースは、さまざまな情報源とアルゴリズムを組み合わせて、高いカバレッジを実現します。これらの情報源には、WHOIS 情報、ネットワーク遅延データ、ネットワーク トポロジ情報、ISP との連携、ネットワーク ソーシャル グラフの分析などが含まれます。ただし、特定の IP 範囲の位置情報はまだ不足している可能性があります。ネットワーク トポロジと遅延情報の利用には、いくつかの制限があります。
(1)グローバルに分散されたマッピングノードリソースが必要である。
(2)すべてのパブリックIPがICMP pingを許可したり、ネットワークトポロジを公開したりするわけではありません。
(3)トレースルートを通じて得られた経路距離は、現実世界の地理的距離に完全には対応できません。しかし、地理位置情報にrDNSを利用することで、これらの制限を克服することができます。
逆DNSからIP接続タイプを導出する
一部の逆 DNS 解決レコードには、接続タイプに関する情報が含まれている場合があります。
- アドスレ: 194.245.146.50: 194-245-146-50.adsl.nrw.net。
- DS-L1000: 201.248.37.20: 201-248-37-20.dyn.dsl.cantv.net。
- ブロードバンド: 95.25.2.183: http://95-25-2-183.broadband.corbina.ru
- ケーブルテレビ:188.156.235.137: BC9CEB89.catv.pool.telekom.hu。
- 動的: 14.3.6.51: http://ae006051.dynamic.ppp.asahi-net.or.jp
この場合、rDNS 情報は、IP 使用シナリオ (住宅、企業、データ センターなど) を調査する方法として役立ちます。セキュリティ製品の場合、通常、さまざまな IP タイプに異なるレベルの保護戦略が適用されます。たとえば、実際のユーザー アクセスの大部分は複数のユーザー間で共有される動的 IP から行われるため、誤検知が発生しやすいため、動的住宅 IP に対してはより慎重で保守的な保護対策を採用する場合があります。ただし、企業専用回線 IP の場合、意思決定コストはそれほど高くありません。
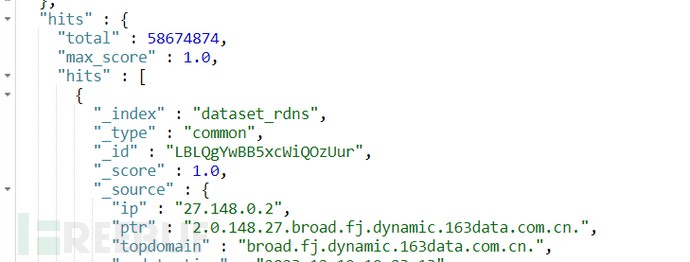
動的 IP は、複数のネットワーク プロバイダーによって IP プールに割り当てられます。そのため、WHOIS 情報やその他のソースから IP が動的であるかどうかを直接確認することは困難です。ただし、rDNS を使用すると、特定のキーワード情報を使用してある程度の判断を行うことができます。簡単な例として、rDNS データベースで PTR レコードにキーワード「dynamic」を含む IP を照会すると、5,800 万を超える IP が直接一致することがわかります。
図3: 一致したIPの数
他のサードパーティの脅威インテリジェンスデータを組み合わせることで、この仮説を予備的に検証できます。
図4: サードパーティの脅威インテリジェンスデータ
もちろん、実際の動的IPの数はもっと多いです。ここでは表面をなぞっただけです。同様に、第2章で述べたように、すべてのIPにrDNSレコードがあるわけではないので、逆引き DNSレコード IP の接続タイプを補完し、強化することができます。ただし、rDNS だけに頼るだけでは完全なデータベースを構成するのに十分ではありません。
ZDNS を使用して IPv4 逆 DNS 解決を実行する
論文「ZDNS: インターネット測定のための高速 DNS ツールキット” は、DNS ライブラリ、コア フレームワーク、構成可能モジュールという 3 つの主要コンポーネントで構成される、高性能でスケーラブルな DNS プロービング フレームワークを導入します。DNS ライブラリは、独自のキャッシュ再帰リゾルバ ライブラリを実装し、再帰クエリ、キャッシュ、検証、パケット交換レコード、および簡素化された DNS 解決を提供します。コア フレームワークは、コマンド ライン操作を簡素化するために使用され、構成可能モジュールは機能拡張を容易にするために使用されます。ZDNS の実装は、いくつかの設計原則に従います。
- 内部再帰: ZDNS は、DNS 操作のさまざまな特性を理解するために再帰解決をサポートしています。これは、パブリック再帰リゾルバが多くの DNS 解決機能を隠蔽し、クエリ レート制限を頻繁に課すことが多いためです。したがって、内部の自己再帰のサポートが必要です。
- 安全: DNS プロトコルは多くの RFC 標準を定義しており、2022 年現在、65 種類を超える DNS レコードがあります。サーバーは誤った構成や悪意のある操作により誤った形式の応答を返すことが多いため、ZDNS はメモリセーフなプログラミング言語を使用し、モジュール式インターフェースをサポートしています。
- 高性能: 外部の再帰リゾルバを使用すると、1 秒あたり 90,000 件の解決が実行され、10 分以内に 5,000 万のドメインがスキャンされ、12 時間以内に IPv4 アドレス空間全体の PTR レコードが解決されます。
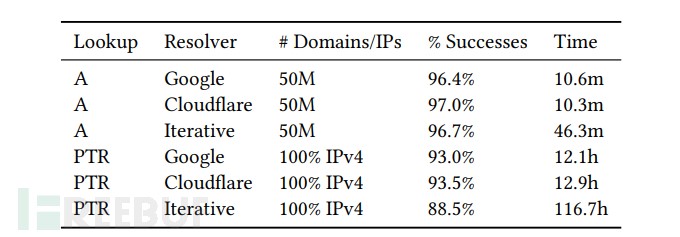
次の図は、ZDNS の解決パフォーマンス データを示しています。
図5: ZDNS解決パフォーマンスデータ
PTR レコードのデータ パフォーマンスだけを考慮すると、Google のパブリック DNS 解決を使用すると、IPv4 アドレス空間全体の解決を完了するのに 12.1 時間しかかからず、93.0% の成功率を達成しました。一方、内部再帰解決を使用した場合、116.7 時間かかりましたが、88.5% の成功率を維持しました。内部再帰解決を使用した場合のパフォーマンスの大幅な低下は、パブリック解決のキャッシュを活用してクエリを高速化できないことと、内部再帰メカニズムが応答を返す前に一定数のクエリを必要とすることによるものです。A レコードと PTR レコードを比較すると、解決数が 5,000 万から数十億に増加すると、ZDNS の成功率は 5% 未満減少します。
結論
リバース DNS (rDNS) テクノロジーは、ネットワーク管理とセキュリティに不可欠なツールであり、IP アドレス情報の強化、地理的位置の識別、接続タイプの識別を強力にサポートします。
rDNS から地理的な位置情報を取得する場合、rDNS レコードのドメイン名を地理的な位置情報データベースと関連付けることができます。これにより、IP アドレスの地理的な位置情報を推測し、地理位置情報および位置認識サービスのデータ サポートを提供できます。これは、ネットワーク ポジショニングやコンテンツ配信ネットワークの最適化などのサービスにとって非常に重要です。
一方、rDNSからIP接続タイプを導出することで、rDNSレコードにあるドメイン名とサービスタイプに基づいて、IPアドレスに関連付けられたアプリケーションとサービスを分類および識別できます。これにより、 ネットワークセキュリティ トラフィック管理により、ネットワーク アクティビティの視覚化と理解が向上します。
IPv4 逆 DNS 解決に ZDNS などのツールを利用すると、大規模な rDNS クエリを迅速かつ効率的に実行でき、ネットワーク管理とセキュリティ分析が容易になります。このようなツールの適用により、実用的なネットワーク情報の収集と分析に対する技術的サポートが提供され、ネットワーク リソースの合理的な利用とネットワーク セキュリティの強化に貢献します。