Distributed Denial of Service (DDoS) attacks have been on the rise in recent years and show no sign of slowing up. With businesses and consumers both feeling the impact of DDoS attacks, mainstream media outlets (i.e. ABC, CNN, and the New York Times) have provided in-depth coverage of some of the larger attacks.
Despite rising awareness of DDoS attacks, their perpetrators are undaunted and continue to level attacks against organizations of all sizes on a daily basis. This is the result of a growing number of wrongdoers easily aligning themselves with nefarious groups. They create or locate readily available tools to launch automated application attacks against any target, from social media and travel websites to global enterprises and government agencies.
Organizations that fall victim to a DDoS attack typically suffer damage in one or more areas: deteriorating customer trust; lost revenue; negative brand impact; or slowed web innovation and expansion. As a result, organizations of all kinds recognize the need to shore up their cybersecurity systems against these easily launched DDoS attacks.
Defining a DDoS Attack
A denial of service attack occurs when web network infrastructure, usually consisting of one or more servers, becomes so overwhelmed with malicious traffic that it utilizes all its resources and can no longer respond to legitimate website users. A distributed denial of service attack amplifies this scenario by launching an attack from multiple computers distributed across the Internet.
Most large-scale DDoS attacks leverage botnets and attack vectors in which to work their way in and ultimately, cause the victim unnecessary downtime. Botnets are computers with breached security that are being controlled and manipulated by the perpetrators of the attack. The perpetrators instruct all computers in the botnet to send fake or malicious traffic to the targeted organization’s web servers. This overwhelms the computers with illegitimate traffic, rendering them incapable of serving legitimate traffic.
What is a DDoS Mitigation Service?
A DDoS mitigation system or service is designed to protect a targeted server or network from a DDoS attack. Using this kind of DDoS protection service combined with threat intelligence, organizations can better prepare themselves against cyber attacks.
How does DDoS Mitigation work?
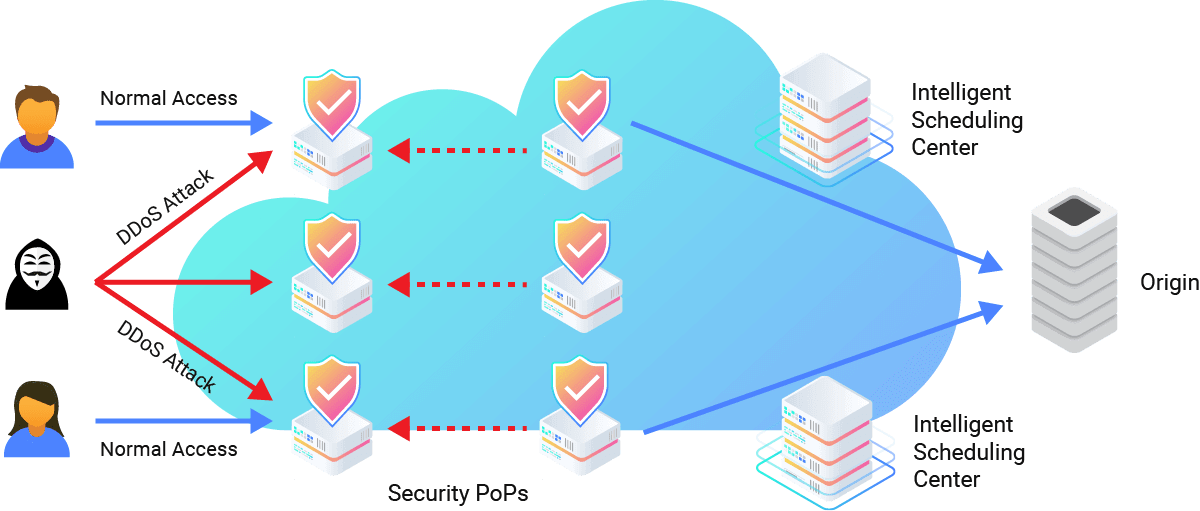
CDNetworks Flood Shield detects and mitigates all types and all layers of DDoS attacks (such as SYN Flood, ACK Flood, UDP Flood, HTTP Flood, etc.) in real-time and simultaneously provides an acceleration service to legitimate users to optimize the user experience. This security solution functions as a shield to ensure the stability and reliability of online services and infrastructures. Flood Shield consists of monitor & alert tools, visualization of attacks, and investigation tools.
Our always-on and inline cloud DDoS protection that offers Scrubbing Center with 15Tbps+ network capacity ensures that we are always defending your website. With automatic traffic profiling and detection, we can identify both cloud-based attacks rapidly and deflect them on the edge of the network.
Pricing for our DDoS mitigation services varies depending on your needs. But rest assured, there are packages to suit all budgets.
What are the Benefits of DDoS Mitigation?
The benefits of DDoS mitigation include:
1. Reduced Downtime – DDoS attacks can cause a website or network to become unavailable to users, resulting in lost revenue and damage to the reputation of a business. DDoS mitigation can reduce downtime by quickly detecting and blocking malicious traffic.
- Improved Performance – DDoS mitigation can improve the performance of a website or network by filtering out unwanted traffic and allowing legitimate traffic to flow freely.
- Protection of Sensitive Business Data – DDoS attacks can be used as a distraction to steal sensitive data. DDoS mitigation can prevent this by blocking malicious traffic and avoiding business data loss caused by service interruption due to DDoS attacks.
- Business Stability – DDoS Mitigation allows businesses to avoid service performance degradation or even service interruption that can be caused by DDoS attacks.
DDoS Attacks – The Cheap and Fast Weapon of Choice
Application layer (DDoS) attacks have become prevalent for three simple reasons – they are cheap, simple to create, and effective. Instructions for creating a botnet can be found easily online.
For example, anyone can perform a Google search on “cheap, automated DDoS” and quickly come up with a botnet creation and launch tutorial. These tutorials come complete with detailed programming instructions to create, launch, and control bots. It even teaches potential perpetrators how to secure their bots and themselves.
The Effects of DDoS Attacks
DDoS attacks can cause massive harm to a network, application or resource by flooding it with a large volume of traffic. They are usually delivered by malicious actors via a botnet or a group of devices controlled together and infected with malware. With the proliferation of IoT devices, the threat landscape has widened and it has only become easier for attackers to launch DDoS attacks.
As resources get used up to meet the incoming traffic requests, they get exhausted and lead to a server failure. For businesses that thrive on providing uninterrupted services to their users, these types of cyber attacks can result in a number of negative consequences including the following:
Interruption of Customer-Facing Applications
When DDoS attacks tie up platform services, they make it impossible to ensure business continuity, creating a poor customer experience. This could result in unsatisfied users, customer churn, or in more serious cases even render key transactions unavailable.
Unwanted/Unplanned Expenses
In addition to the revenue lost due to customer churn, DDoS attacks can also create additional expenses for businesses in the form of website and data center recovery costs.
Daily Operational Applications at Risk
It’s not just customer-facing applications that DDoS attacks can bring down. Even business applications that help you with daily operations can be affected. Email automation, CRM tools, payroll processing software, and other internal applications key to running your business can be affected by DDoS attacks.
Weakened Security
DDoS campaigns don’t end when they manage to compromise some servers or services in your organization. The flood of network traffic will continue to overwhelm your other systems until more robust DDoS defenses are put in place. This is a period where your network security infrastructure can be taken advantage of by hackers to target other, more sinister types of attacks.
Reputation Damage
Sometimes the negative impact of DDoS attacks on your business isn’t monetary. When key public-facing applications are down and websites or apps are slow to load, it can leave a bad impression of your brand among customers. In fact, 57% of companies surveyed by NETSCOUT’s WorldWide Infrastructure Security Report think that DDoS attacks affected them most with damage to their brand more than operating expenses.
The Most Common Types of DDoS Attacks
While there are many various types of DDoS attacks in existence, some of the most commonly used today are those of volumetric attacks. These attacks target networks and send high amounts of traffic to them, in an effort to overload its bandwidth capabilities.
Flood Attacks
Flood attacks, such as GET/POST flood, SYN flood, and UDP flood, are some of the easiest to launch and to understand. The reason they’re referred to as flood attacks is they effectively “flood” a targeted web server with requests, causing the server to respond and open connections to the compromised computers (botnet) that are making the requests.
By not responding back to the targeted server, the botnet holds open all server connections as the targeted server awaits responses. Eventually, the targeted server maintains so many open connections that it runs out of available ports to serve legitimate users, causing major service outages.
ICMP Flood Attacks
A variation of the standard flood attacks is the Internet Control Message Protocol (ICMP) Flood, which also goes by names such as Smurf attack, Ping flood, and Ping of Death. Perpetrators of this type of DDoS attack spoof the IP address of the targeted victim, then use that IP address to send out a broadcast of requests to a network of computers. When the network of computers responds, the targeted victim’s network layer becomes flooded with response traffic, thereby blocking legitimate user traffic from reaching the victim’s machine.
DNS Amplification
A third and increasingly common, type of flood attack is called a DNS amplification attack. This type of attack works by spoofing the IP address of the targeted victim’s server DNS and using it in communications with improperly configured DNS resolvers, called Open DNS Resolvers.
Open DNS Resolvers reply to all DNS requests, often with large amounts of data, without confirming their origin. This combination of many machines and large responses makes Open DNS Resolvers ideal resources for launching a large-scale attack. Moreover, they offer ample opportunity to hackers, as noted by The Open Resolver Project, which currently tracks over 27 million Open DNS Resolvers in operation today across the Internet.
With so many open resolvers, each with the ability to transmit large amounts of traffic, it is easy to see why DNS flood attacks occur more often today than ever before.
If you’d like to learn more about XOR.DDoS attacks, please read our blog article: Understanding XOR.DDoS attacks
The ‘Who’, Where, and Why Behind DDoS Attack Origination
DDoS attacks are on the incline and are quickly becoming the most common type of cyber threat. In addition to the actual rise in the number of attacks, the severity of these attacks is also a growing concern. The latest trend now focuses more on a shorter attack duration, but with a larger packet-per-second attack volume.
As for who perpetrates all these DDoS attacks, that’s a difficult puzzle facing the law enforcement community. The profile of DDoS attack perpetrators is ever-shifting, depending on the nature of current issues and opportunities presented. That said, the most common DDoS attackers include the following:
- Organized crime syndicates
- State-sponsored wagers of electronic warfare
- Businesses attempting to weaken competitors
- Politically motivated cyber terrorists (hacktivists)
- Extortionists
- Hackers seeking profits
- Individuals out for a thrill
As for why these attacks occur, that’s a mixed bag. But typically, attackers are motivated by one or more of the following:
- Extortion – Money is one of the main reasons behind DDoS attacks. Perpetrators use these attacks, or at least the threat of them, in an attempt to extort money from their target.
- Business feuds – Some unscrupulous businesses use DDoS attacks to take down their competitors’ websites at crucial moments – i.e. just before a big sale is due to start.
- Cyberwarfare – This is when the government authorizes a DDoS attack on an enemy country’s infrastructure.
- Ideology – Many DDoS attacks simply because the hacker disagrees with the website’s ideology.
- Boredom – Many cyber-vandals, hackers, or script-kiddies, do what they do simply because they can. Typically these perpetrators are nothing more than bored individuals looking for their next adrenalin rush.
Traditional Web Infrastructure Cannot Handle DDoS Protection
Just as traditional web infrastructure has proven inadequate for handling large amounts of legitimate web traffic, it also falls short in fending off most DDoS attacks. Both the origin and overflow infrastructure lack the resources for all but the smallest of DDoS attacks.
The typical enterprise’s server and switch capacity fall far short of the capacity required for mitigating a DDoS attack. In today’s environment of tightened IT security services budgets, most organizations simply cannot afford to expand their web infrastructure in the manner required to protect their business against such attacks.
In addition, the costs of establishing additional data centers just to defend against DDoS attacks make little sense. For this reason, organizations are turning to managed hosting providers and/or content delivery networks (CDNs) with DDoS absorption capabilities to serve their websites to a global audience.
Choosing CDN With DDoS Absorption
Managed hosting providers and CDNs are not equal when it comes to DDoS absorption. First, the larger managed hosting providers with the capacity needed to absorb an attack often exist on the very networks frequently experiencing DDoS attacks, or at the very least carrying their traffic.
Moreover, managed hosting providers do not span across different networks as the larger CDNs do, making them unable to match global CDNs in their ability to shift network usage quickly when an attack on specific networks occurs.
Establish a DDoS Mitigation Solution Now, But Plan For Evolution
Given the reality of today’s online world – that high-volume DDoS attacks will continue to strike a wide variety of organizations across industries and geographies, professionals charged with maintaining an operational web presence must act fast to shore up their web infrastructure.
At the same time, however, they should plan carefully and leverage a service provider that has a track record for evolving its infrastructure and services in line with the evolving nature of the online world. Only this type of strategy will enable continued online innovation in a manner that protects ongoing business today.