The ever-increasing needs for DDoS mitigation service
Through our daily communication with our customers and retailers, we have realized that the Japanese market continues to show a greater need for security services. We not only receive inquiries from security-conscious companies but also organizations from unexpected fields.
We often hear “Everything will be fine with CDN DDoS mitigation, right?”. However, this is not entirely correct.
In this guide we’re will explore the relationship between content delivery networks and DDoS attacks to correct this misunderstanding. We will also explore what level of protection is required for businesses looking to fend off distributed denial of service attacks.
What are DDoS attacks?
Firstly, let us explain what DDoS attacks are and how they work.
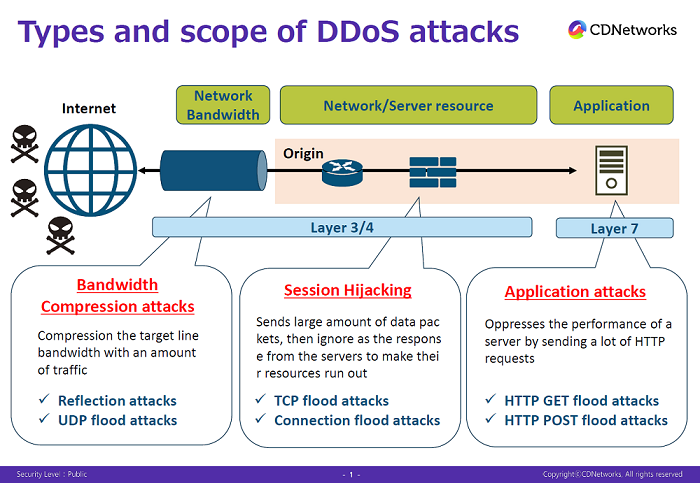
DDoS attacks are cyber attacks against network layers (layer3/4) or application layers (layer7). There are many methods for each attack, but they all bring about losses by interfering with what the web site shows.
Bandwidth compression attacks (Layer3/4)
These attacks overload the target servers with an amount of traffic that they cannot ordinarily serve, leading to a service blackout for the targeted website. Typical examples of these attacks are the “Reflection attack” and the “UDP flood attack.”
Session hijacking (Layer3/4)
In this variation, the attacker sends a large amount of data packets, then ignores the response from the servers to make their resources run out. The typical examples of these attacks are the “TCP flooding attack” and the “SYN flood attack.”
Application attack (Layer 7)
This is an attack that oppresses the performance of a server by sending a lot of HTTP requests. Typical examples are the “HTTP GET flood attack” and the “HTTP POST flood attack.”
Is CDN helpful as a DDoS mitigation?
Now we have introduced the types of DDoS attacks, we will now look at whether CDN is effective in defending against them. Let’s consider this, looking at each type of attack.
Bandwidth compression attack (Layer3/4)
CDN is a service made for handling large amounts of legitimate traffic, maintaining stable data transmission. Although having many broad lines will support service, to get straight to the point, it won’t be enough to provide defense against DDoS attacks completely.
We must remember that CDN is only a sharing service.
Of course, it is no problem if it is inside the scope of the line’s capacity and doesn’t interfere with other customers’ usage. However, if it starts to affect other customers, as a CDN provider, it is necessary to deal with the problem. In some cases, CDN vendors need to exclude an attacked website from their CDN service, as blocking individual IP addresses won’t be enough.
Session hijacking (Layer3/4)
As mentioned above, CDN is a service made for handling large amounts of traffic, maintaining stable data transmission. Here, we utilize many decentralized high-spec HTTP servers, but it is also not enough.
As previously mentioned, we need to remember that this is a sharing service.
If it is within the CDN server’s limits, there is no problem. On the other hand, if it begins affecting other customers, you will need to act to deal with the situation.
Application attack (Layer 7)
Skipping straight to the conclusion, it’s the least effective against application attacks.
There is no problem if you cached in CDN, even if you receive a large amount of HTTP GET flood attacks. However, as the attack might be taken as transactions traffic, traffic burst fee may occur unexpectedly.
Regarding contents that are not, or should not be cached, requests will be sent to the customer’s web server, as it is not processed by CDN.
CDN security service has DDoS protection features
And so, it is not enough to use only a CDN for DDoS mitigation.
Each CDN vendor has released CDNs with DDoS protection features. Recently, there are several methods and charging systems, such as on-demand real-time type, always block, and those which can cope with protocols other than TCP. With those products, users can choose services based on their environment and budget. On top of the usage of CDNs, if you use DDoS mitigation by a CDN vendor, you can create an effective security system.
CDNetworks offers the cloud type DDoS mitigation service, called “Flood Shield”. Whether you are thinking about introducing security measures or adding them to the existing CDN service, our sales team will offer the best plan for you. Please do not hesitate to drop us a line.
Read More: CDN Benefits
CDNetworks – “Cloud security DDoS.”
“Cloud security DDoS” is the cloud-type mitigation service against DDoS attacks which we have achieved with a large distribution capacity and a world-wide network of data centers. We responded to, and succeed in protecting from almost all of the DDoS attacks that happened last year, with mitigation against attacks on network layer 3/4 and application layer 7.
When huge attacks happen, our users do not suffer from service stoppage or downtime, often because our CDN platform absorbs attack traffic, working alongside our web application firewall (WAF) meaning service as usual. Thus, you can keep the availability, speed, and stability of your web sites.
If you are thinking about using our CDN DDoS mitigation service, please do not hesitate to ask us.