As the trend toward remote workers and digital transformation gains momentum, the demand to work from anywhere on any device is becoming the new normal. With this new work model comes an assortment of security challenges. Foremost is the ability for enterprises to identify the individuals and devices seeking access to their networks and resources. Given today’s hybrid environment, it becomes extremely difficult, if not impossible, for enterprises to secure access for their remote workforce using outdated VPN tools whose static password-authentication methods are limited to identifying only users. For this reason, an increasing number of organizations are adopting a Zero Trust approach to limit risks of unauthorized access, insider threats, and malicious attacks.
It’s Time to Replace Outdated VPN
The inability to verify user identities, devices, and other critical factors puts an organization’s network and resources at risk. To address this vulnerability, enterprises are starting to replace outdated VPN deployments with Zero Trust network access solutions to safeguard their sensitive information from data breaches, database deletion, ransomware attacks, web trojans, and other cyberattacks.
What is Zero Trust and CDNetworks’ ESA?
Rooted in the principle of “never trust”, Zero Trust is a strategic proactive trust-and-verify approach to cybersecurity. Zero Trust eliminates implicit trust by authenticating every user and device on the network, and authorizing them to access only the applications and data they need through every interaction within the company.
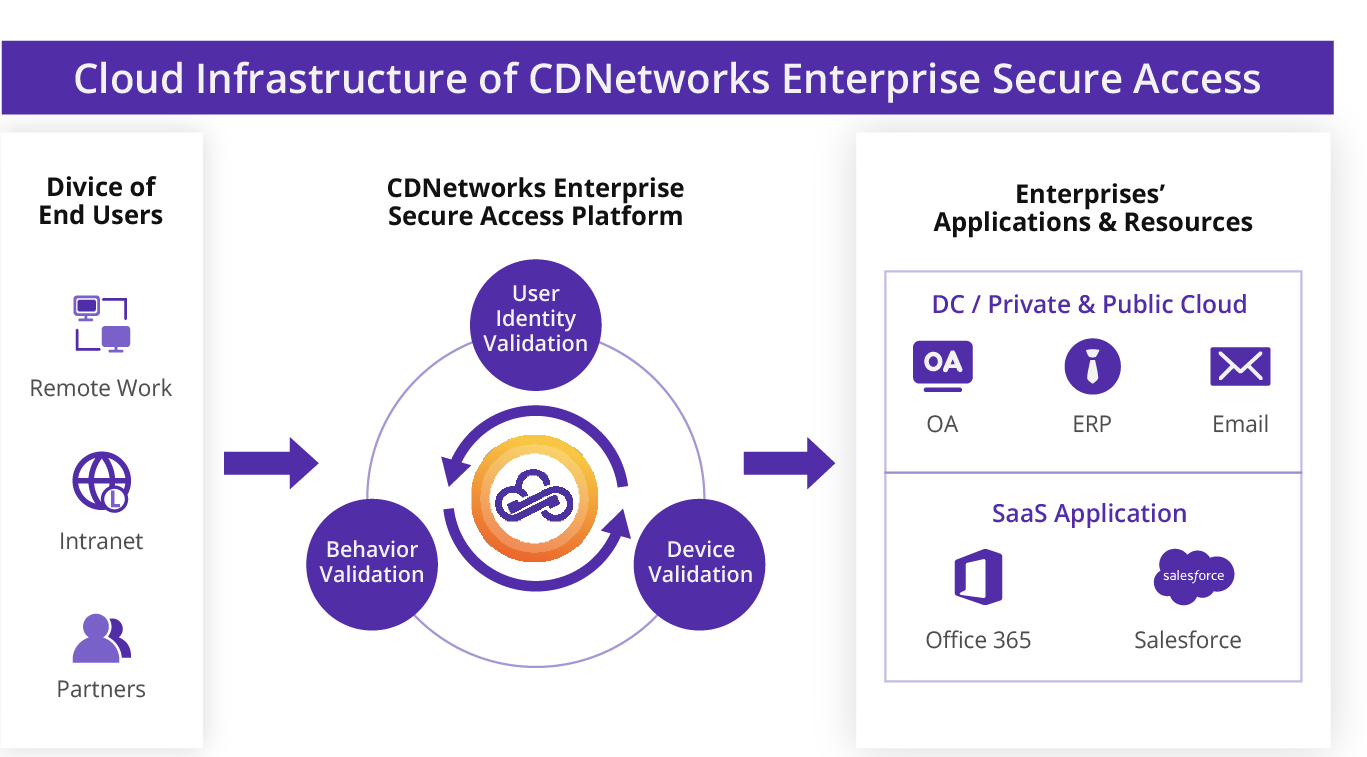
CDNetworks’ Enterprise Secure Access (ESA) is a premier cloud service that provides enterprises with secure remote access. ESA uses a Zero Trust implementation with a Software-Defined Perimeter (SDP) infrastructure to protect business networks and data from intrusion and exploitation.
How CDNetworks’ ESA Secures Hybrid Network
Right People, Right Access, Right Data
ESA is a Zero Trust access solution that checks user identity, device security, and user behavior to ensure that only authorized users and devices are granted access to appropriate enterprise applications and data. But Zero Trust doesn’t stop there: It continuously evaluates user behavior, identification, device security, and threat intelligence to adapt to shifting security paradigms.
- User Identity
There are two core enforcement pillars enabling Zero Trust‘s right access. The first is the need to enforce user privileges. The context in which the user is requesting access plays a major role in Zero Trust policies. It includes factors such as identifying the type of content being accessed and the application being requested in order to verify user privileges. The second pillar is multifactor authentication (MFA). MFA leverages multiple identity-verification protocols beyond just usernames and passwords to mitigate threats of a credential-related compromises.
- Device Security
Based on a security baseline, ESA simultaneously monitors security status, device IDs, anti-virus scans, domain access control, and weak passwords for user devices to secure access to sensitive information.
- User Behavior
ESA allows enterprises to manage user privileges by establishing a preset trusted posture, and then optimizing it as necessary by evaluating user behavior. All along, only trusted users are permitted access to the application or resources to which they have been granted access.
Only after validating user identity, device security, and user behavior will CDNetworks’ ESA authorize users and trusted devices to ensure that everyone and every device stay within their allowed usage.
Making Your Hybrid Networks Invisible and Secure
Remote access to networks and resources is not limited to an enterprise’s workers. Today’s organizations collaborate with large numbers of outside sources, such as vendors, partners, and third-party workers coming and going without geographic restriction. To accommodate third-party ecosystems, enterprises must expose their internal systems to a larger audience, opening the door for potential cyberattacks and breaches. That’s why CDNetworks’ ESA shields the origin server’s IP address and ports behind a secure gateway, eliminating the attack surface to stop cyberthreats and data loss in their tracks before they have a chance to mount an attack.
In this way, ESA protects your application and data effectively while following the principle of “Never Trust, Always Verify.” The foremost advantage of ESA is that it is easy to implement and deploy, bringing about transformation more quickly at a lower cost and with reduced strain on security resources. Start your journey to Zero Trust to protect your critical resources today!
Get Started with CDNetworks’ ESA
CDNetworks’ Enterprise Secure Access solution delivers continuous verification, with no trusted zones, credentials, or devices at any time, to continuously enforce “Never Trust, Always Verify” verification to broad sets of assets.
Several key elements must be in place for this to work effectively:
- Identify internal identity-management systems.
- Develop an adaptive access control strategy:
- Define security authentication level of applications.
- Define device security posture.
- Define user-privilege policy.
- Install an ESA connector to integrate applications to the ESA security gateway.
- Integrate SaaS applications to the ESA security gateway.
- Integrate identity management system to the ESA control center.
- Apply adaptive access control policies to the ESA control center.
- Optional: Install an ESA client on customer devices (browser-based access is also supported).
- After deployment, analyze user behavior and security posture to continuously optimize access security policies.
Every organization has unique challenges due to its business, digital transformation maturity, and current security policies. CDNetworks’ Enterprise Secure Access solution can be tailored to meet specific needs, reduce security complexities, and reduce time to identify and remediate breaches while reducing costs and delivering a return on investment.
With its proven track record of success, CDNetworks continues to protect data for organizations covering a myriad of industries, including Government, Finance, Healthcare, Education, and Energy. To learn more about how we can help your business, please contact us to get a free trial of CDNetworks’ Enterprise Secure Access solution.
About CDNetworks
As a global-leading Content Delivery Network (CDN) and Edge Service provider, CDNetworks delivers fully integrated cloud and edge computing solutions with unparalleled speed, ultra-low latency, rigorous security, and reliability. Our diverse products and services include web performance, media delivery, enterprise applications, cloud security, and colocation services — all of which are designed to spur business innovation.