The pandemic-related lockdowns increased online traffic and cloud application adoption in the past two years. The increase also attracted cyber-attacks on web applications. According to the CDNetworks security report, web application attacks surged 141.3% in the past year alone. With many companies continuing to grow their investment in cloud-based applications to expand their business, web attack threats will only increase. Protecting web applications from web exploits, compromise, and attacks have never been more important for companies with an online presence.
CDNetworks, a leader in the cloud content delivery industry, released its latest cybersecurity solution, CDN Pro with Web Application Firewall (WAF), this September to help customers protect their online businesses against the wave of internet web application attacks.
CDN Pro is CDNetworks’ Edge Cloud product for global content delivery. Edge Cloud is built from the ground up with robust features that protect against security breaches. By 2022, CDN Pro alone has successfully handled some of the world’s most brutal DDoS attacks with a bandwidth of 1.2Tbps and a request rate up to 35Mrps.
CDNetworks’ WAF is a cloud-based service protection solution. Using intelligent automation and unparalleled capabilities, backed by qualified cybersecurity experts and advanced scanner, CDNetworks’ WAF patches security flaws before attackers gain access to them, eliminating vulnerabilities before attackers can exploit them.
By bundling CDN Pro with CDNetworks’ WAF uniquely enables the CDN Pro WAF solution to defend against web application attacks efficiently and effectively without sacrificing performance.
CDN Pro on Security
The CDN Pro platform is designed with security in mind. It boasts built-in security features as well as programmable security features.
Layer 4 DDoS Mitigation
CDN Pro is built on the Edge Cloud Computing platform. At the entry point of every edge, a Point of Presence (PoP) is a high-performance layer 4 distributed denial-of-service (DDoS) firewall. The firewall consists of a group of machines that analyze incoming traffic at line speed. Based on regularly updated rules, the firewall rejects suspicious packets that may put web application services at risk and forwards only “safe” packets to the origin servers behind the firewall. The firewall is enabled by default for all edge services and is transparent to all CDN Pro customers.
Layer 7 Protection
For the network OSI model layer 7 traffic, CDN Pro is equipped with real-time monitoring to detect unusual behaviors of the incoming traffic. Once an attack is identified, defense strategies are deployed at both layer 4 and layer 7 to mitigate the impact on normal web application traffic.
Access Control with CDN Pro Programming
With its Edge Cloud posture, CDN Pro is a programmable content delivery platform. It uses open-source NGINX scripting language with enhanced and proprietary directives. Customers can use its integrated programming interface, Edge Logic, to configure access control rules to protect content from unauthorized users and mitigate common layer 7 attacks.
The followings are a few examples of how to set up access control rules with CDN Pro programming:
Restrict client IPs with ‘allow’ and ‘deny’ instructions:
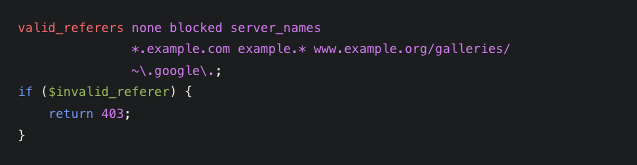
Check and control based on the ‘Referer’ request header with ‘valid_referers’:
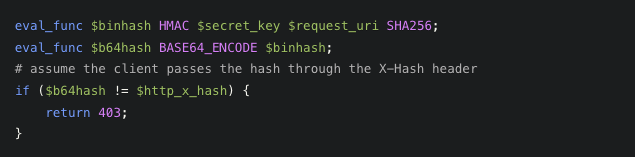
Use the proprietary directive ‘eval_func’ to validate HMAC authentication with SHA-256 for accessing control:
WAF Defense
CDNetworks’ WAF is a cloud-based web application firewall that protects web applications from common web exploitations and compromises. It supports managed rules as well as customized rules. Built with a central cloud defense engine, WAF constantly learns and protects web applications from new malicious actors and attack vectors, keeping businesses safe and available amid the continual threats posed by increasingly virulent cyberthreats.
OWASP Top 10 Threats
CDNetworks’ WAF is a full-featured threat defense solution. It includes hundreds of signatures and policies to defend against OWASP top 10 threats, such as injections, directory traversal, and XSS.
Rate Limiting
WAF supports a Rate Limiting feature that reduces risks of brute-force and other automated attacks by limiting the number of HTTP requests allowed to web application origin servers during a fixed period.
Customer Rules
To maximize protection of customer assets, WAF supports flexible customer rules, multiple policy enforcement modes, and customized policies to cover any potential threat to web applications.
Access Control
Customers can set access control rules on the WAF configuration portal to block unwanted users and potentially bad traffic by IP address, HTTP headers, and other parameters to avoid web application attacks.
Control and Monitoring
The cloud-based WAF platform allows almost instant deployment of policy changes. In addition, the real-time portal dashboard allows customers to get immediate and intuitive views of security status.
Enhanced Security with CDN Pro and WAF
The CDN Pro with WAF solution provides centralized and multi-level protection for your web applications. It defends your web applications against common exploits and vulnerabilities while increasing availability for your customers.
Deployed on its global edge servers, the CDN Pro with WAF solution stops malicious attacks close to the attack sources before they get close to your origin web applications. As a result, you get global protection without sacrificing performance.
The following figure shows the CDN Pro WAF-enhanced solution for a typical origin web application:
The following steps describe how the solution works:
1. An end-user initiates a request for content from your web application.
2. CDN Pro Global Service Load Balancer (GSLB) inspects the request traffic based on the pre-defined layer 4 and layer 7 policies for any security risks. If the request does not pose a threat, GSLB routes the request to the edge location that best serves the request – usually the nearest CDN Pro edge location for the end-user.
3. At the edge location, CDN Pro checks whether the requested content is cached at the edge location. If the content is cached, CDN Pro returns the cached copy to the end-user.
4. If the content is not cached, CDN Pro processes the request based on edge logic programming, security policies, or access control rules to decide how to process the request. If any rules are violated at the CDN Pro level, CDN Pro drops the request and replies to the end-user with an error status.
5. If CDN Pro decides to move forward and go to the origin to fetch the content, it could add the custom header X-Forwarded-For with real client IP or some other agreed-upon headers between CDN Pro and WAF, and then forwards the request traffic to the WAF.
6. The WAF inspects the incoming request traffic to check against the WAF configuration and pre-defined policies.
If the request violates WAF policies, WAF blocks it and responds to CDN Pro with an error status to return to the end-user.
7. If the request does not violate WAF rules, WAF allows the request to go to the origin, fetches the content, and forwards the response back to CDN Pro and the end-user.
Conclusion
Leveraging comprehensive security features and high-performance global infrastructure, CDN Pro and WAF work together seamlessly to create a flexible, layered security perimeter to protect your web applications from internet threats and attacks.
To get started protecting your web applications and learn more about CDN Pro and WAF products, please contact CDNetworks Sales.