Distributed Denial of Service (DDoS) attacks continue to evolve and amplify in scale and complexity. Many recent studies show that DDoS attacks are becoming more frequent, sophisticated and powerful. In fact, the largest recorded DDoS attacks have reached over 1.4 Tbps in size and they continue to rise due to the proliferation of IoT devices.
DNS amplification attacks are one of the most dangerous types of DDoS threats. These attacks leverage vulnerabilities in network protocols to generate a large amount of traffic directed at a targeted website or service, overwhelming its servers and making the site unavailable to legitimate users.
What is a DNS amplification attack?
A DNS amplification attack is a type of DDoS attack in which an attacker makes use of open DNS resolvers to overload a target server or network with traffic.
DNS resolvers are servers that receive queries from web browsers and other applications. For example, they can receive a hostname and track down the IP address for that hostname. DNS amplification attacks are reflection-based volumetric DDoS attacks where a response from DNS resolvers is elicited to a spoofed IP address. Vulnerabilities in such DNS servers are exploited to turn initially small queries into much larger payloads, thereby “amplifying” the traffic and bringing down the victim’s servers.
How does a DNS amplification attack work?
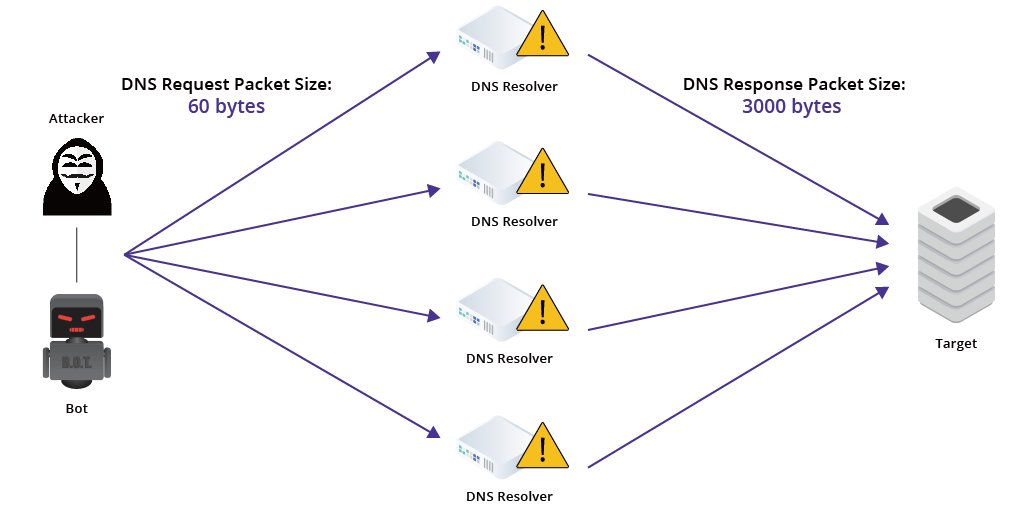
DNS amplification attacks rely on a server sending responses that are disproportionate to the original packet request sent to it. In these attacks, the perpetrator sends fake DNS queries with a forged IP address to an open DNS resolver.
The DNS resolver is promoted to reply back to the address in question with a DNS response. As more such fake queries are sent to the address, with additional amplification using botnets, the DNS resolvers also start replying back simultaneously.
This means that the victim’s network gets flooded with a large number of DNS responses and gets overwhelmed. The amplification factor in these attacks refers to the ratio of the amplified traffic to the traffic the attacker generates.
How dangerous are DNS amplification attacks?
As is the case with most DDoS attacks, DNS amplification attacks can be very dangerous because they can generate a large amount of traffic directed at a targeted website or service. This overwhelms its servers and makes the site unavailable to legitimate users. The amplification factor in these attacks can be significant, with some attacks being able to generate hundreds of gigabytes or even terabytes of traffic.
This can cause significant disruption to the targeted website or service, resulting in lost revenue and damage to the organization’s reputation. Additionally, the large volume of traffic generated by these attacks can also consume network resources and cause congestion, impacting the availability and performance of other services on the same network.
Famous DNS amplification attack events
Many recent high-profile DNS amplification attacks show how dangerous such threats can be to organizations. In 2013, for example, the Spamhaus attack targeted the anti-spam organization Spamhaus, and was launched using a combination of DNS and NTP amplification attacks. This was one of the largest attacks recorded at the time, reaching peak traffic of over 300 Gbps.
More recently in 2020, there was an amplification attack on thousands of Google’s IP addresses that lasted for six months. The attack leveraged several networks to spoof packets to 180,000 exposed servers including DNS, which would then send large responses to Google. Peaking at a high of 2.5Tbps, this attack was four times larger than the previous record of 623 Gbps attack from the Mirai botnet in 2019.
There have also been massive attacks targeted at cybersecurity and content delivery network providers that made use of botnets and compromised IoT devices. These attacks also continued to peak at over 1.2 Tbps.
How to mitigate DNS amplification attacks?
Mitigation measures against amplification DNS amplification attacks must involve a number of different steps. Some of the most critical ones include implementing rate limiting and securing open network services. Rate limiting can limit the number of requests that a server can receive from a single IP address while securing DNS, NTP and other services can ensure that they only accept requests from trusted sources.
In addition, organizations can deploy DDoS protection solutions, such as firewalls or specialized DDoS mitigation appliances, which are designed to detect and filter out malicious traffic before it reaches the targeted servers. Application Shield is a cloud-based web service protection solution from CDNetworks that integrates Web Application Firewall (WAF), DDoS protection and CDN acceleration. It is capable of protecting web applications from malicious actors and against various threats including site scanning activities, web trojans, account take-over attempts, credential stuffing attempts and other web application attacks.
Cloud-based DDoS protection services can also absorb and filter out a large amount of traffic before it reaches the targeted servers. This can help to ensure that the targeted servers do not become overloaded and unavailable during an attack. CDNetworks provides businesses with Flood Shield, a comprehensive cloud-based DDoS protection service that helps you defend against various types of DNS amplification attacks. Not only does it offer protection in real time, it also simultaneously provides an acceleration service to legitimate users to optimize the user experience.
With the help of Flood Shield or Application Shield, firewalls can be deployed between your origin sites and the public network. There will also be sufficient nodes and bandwidth resources to clean a large number of malicious TCP/UDP links, which will ensure normal operation of your source site. Techniques like rate limiting, port limiting and threat intelligence are also part of both Flood Shield and Application Shield and these can help to mitigate all kinds of DNS amplification attacks in real time.


