Are you still tirelessly searching for a cloud security platform that seamlessly integrates with the various protective capabilities of WAAP? A platform that allows your business to swiftly deploy and activate all sorts of WAAP features through a consolidated console platform when facing attacks or threats, and leverages the powerful adaptive protection capabilities brought by AI to quickly fend off the most challenging security threats? If all these concerns are on your radar, CDNetworks Cloud Security 2.0 stands out as your prime choice. But the benefits it brings to enterprises go far beyond this. That’s why we need to share in this blog how it effortlessly fortifies your business against threats and how it seamlessly fits into your daily operations.
The Evolution of Cloud Security 2.0
For businesses today, choosing a cloud security platform is mainly about picking one with the most advanced platform architecture. Take security protection, for example. Early on, companies used traditional perimeter protection. But because perimeter protection is limited by space, cost, and cannot adapt to the fast growth of a company, it soon became inadequate. This led to the creation of cloud-based security platforms, which can overcome these limitations and allow for quick deployment as a business grows. And before CDNetworks launched new Cloud Security 2.0 platform, all of our cloud security products (like Flood Shield, Bot Shield, WAF, API Shield) were built on a cloud-based architecture.
However, as cyber threats become increasingly complex and diversified, enterprises no longer just need to manage multiple cloud security products to achieve comprehensive WAAP capabilities. Instead, what they need is a cloud security platform that integrates all WAAP capabilities. This is where CDNetworks Cloud Security 2.0 comes in as a multi-layer protection solution that achieves a closed-loop risk management for web applications and APIs. This means it offers a unified platform for all previous cloud security products, provides unified visibility with one portal and one log tool, and features a managed protection mode powered by AI technology. An important aspect to highlight is its user interface (UI) design, which aligns well with organization’s daily routine, directly helping businesses boost operational efficiency. And these enhancements are all thanks to a meticulously designed system architecture.
The Architecture of Cloud Security 2.0
As illustrated below, the CDNetworks Cloud Security 2.0 platform boasts a Unified Protection Engine. This engine not only fully integrates the protective capabilities brought by the 4 Scenario-based Protection Modules and 5 General Modules, but it also encompasses the AI central engine and its intelligence mechanisms. This integration ensures all key components of the system work in harmony and bolster each other, creating an efficient operational mechanism. Next, we will use this architecture diagram as our foundation, starting from the bottom layer of resources to gradually explain the platform’s operating principles. The intention behind this unique introduction is to help enterprises better understand the significant platform changes and new protective capabilities brought by CDNetworks Cloud Security 2.0.
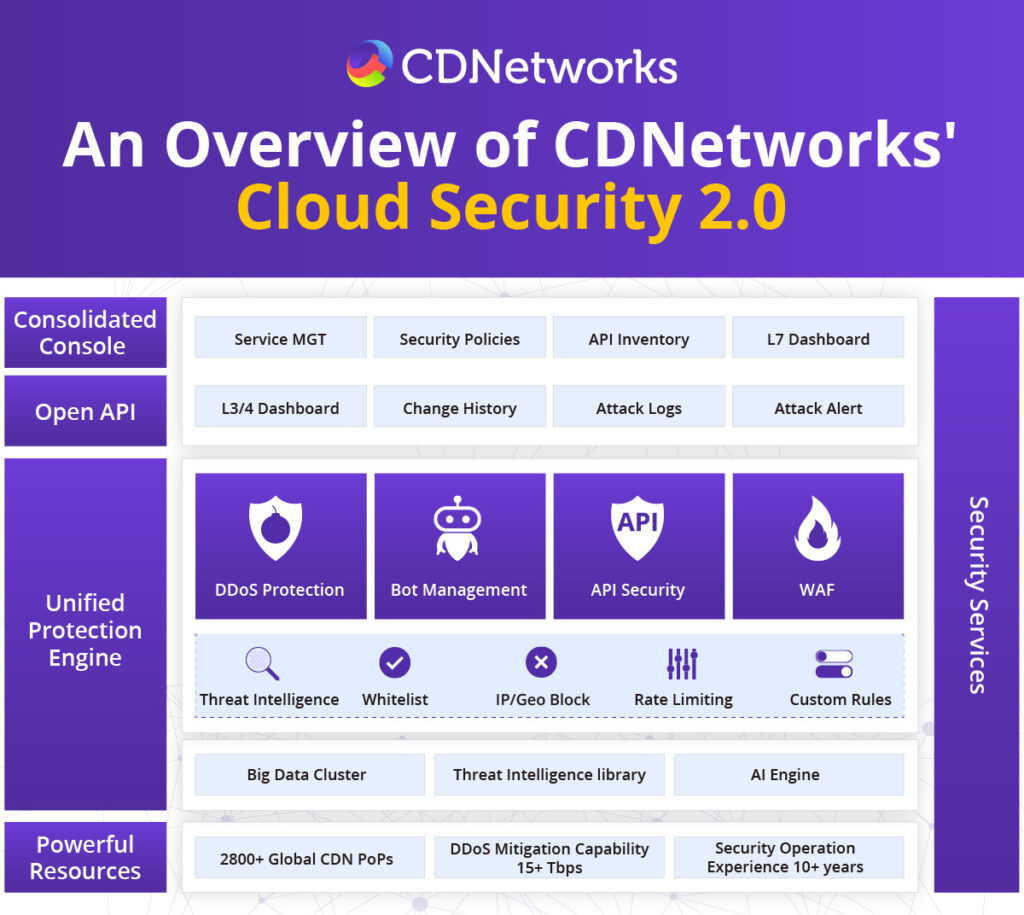
What’s New for Cloud Security 2.0?
-
Powerful Resources and Share-use Intelligence Analysis Model
First, let’s discuss the resources. Similar to other cloud security products, CDNetworks Cloud Security 2.0 is built on a global network of over 2,800 Points of Presence. Through intelligent scheduling between these PoPs and the corresponding infrastructure resource reserves, CDNetworks boasts over 15 Tbps of DDoS Mitigation Capabilities, enabling enterprises to defend against the volumetric DDoS attacks.
Meantime, leveraging the power of big data, CDNetworks utilizes Machine Learning to analyze over 3 billion daily attack samples collected from its globally distributed CDN nodes. These analyses feed back into its Threat Intelligence Library, making it a crucial intelligence source alongside third-party intelligence, enterprise intelligence, and open-source intelligence. This approach ensures that the attack intelligence is more accurate and meaningful.
Building on this foundation, CDNetworks leverages its extensive experience in serving enterprise customers across various industries to effectively process intelligence using evaluation mechanisms such as Feature Engineering, Association Analysis, and Risk Classification. This processed intelligence can be directly applied to specific use cases, such as low-frequency L7-level DDoS protection, Bot risk scoring assistance, and sharing risk IP lists across the cloud and origin servers. These applications provide enterprises with a reliable basis for defending against cyberattacks, particularly zero-day or one-day attacks. Furthermore, the upgrade of the intelligence mechanism significantly enhances the effective operation of the AI central engine and adaptive protection, which will be discussed later.
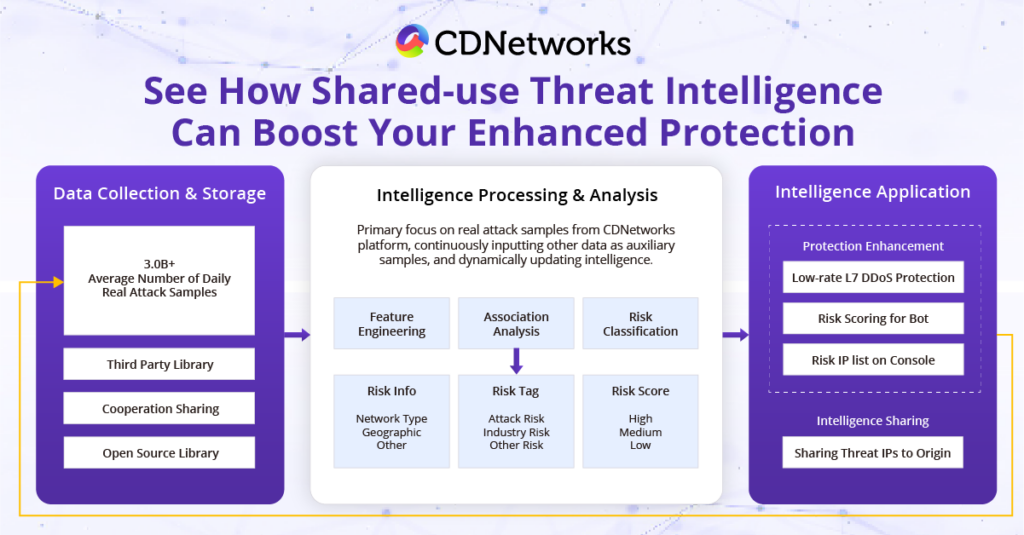
-
AI Central Engine and Adaptive Protection
Unlike the intelligence gathering mechanism, which aims for comprehensiveness, enterprises often seek precise protection in network security to ensure that security services support business operations and even enhance the customer experience.
Based on this, CDNetworks actively embraces change by introducing AI and constructing an AI central engine grounded in the business baselines of enterprises. When businesses integrate protection, the AI first learns from the enterprise’s business baseline, distinguishing between normal traffic, attacks, critical information, SSL/TCP/IP parameters, and other relevant data within the online business. By combining these insights with auxiliary judgments derived from intelligence analysis, the AI can effectively identify and mitigate attacks, thereby improving the accuracy of protection. Once the AI has completed its learning process, it can also provide adaptive suggestions for default security protection rules based on the current state of the enterprise. This proactive approach helps enterprises prepare for potential attacks before they occur.
Certainly, the greatest utility of AI lies in its role in detection and the automatic deployment of protection rules within adaptive defense mechanisms, thereby enabling continuous combat against attacks. For example, in the protection against Advanced Bots, based on machine learning, big data analysis, and CDNetworks’ extensive experience in Bot management, the AI Central Engine can effectively detect and prevent Advanced Bots attacks based on behavioral models (as shown in the diagram). Similarly, in the face of various types of DDoS attacks, AI proves equally powerful, as it can automatically deploy protection rules to achieve Adaptive DDoS Protection.
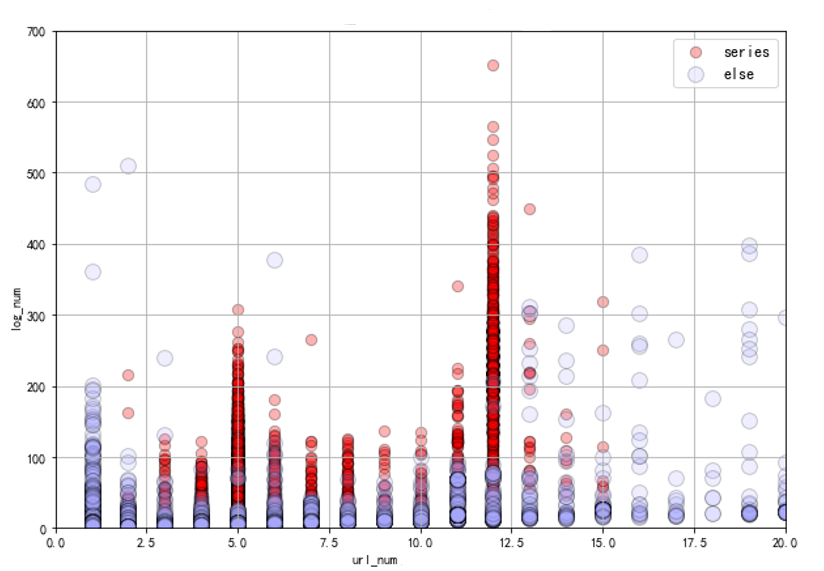
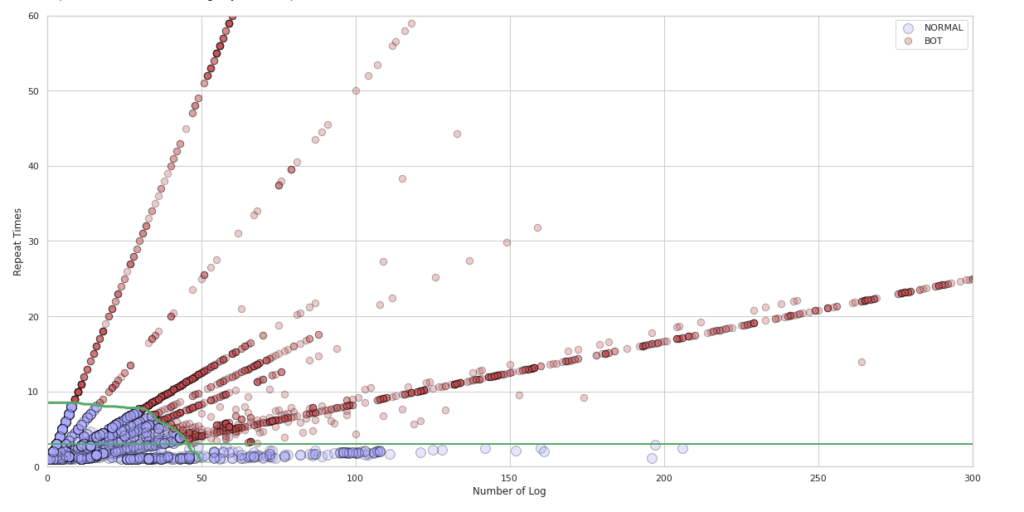
-
Unified Protection Engine and Advanced WAAP Protection
It can be said that with its powerful AI central engine and significantly enhanced capabilities in intelligence collection and analysis, the CDNetworks Cloud Security 2.0 platform’s Unified Protection Engine has made remarkable improvements in protection capabilities. To ensure that these enhancements in protection capabilities genuinely benefit enterprises, the CDNetworks Cloud Security 2.0 platform has seamlessly integrated its five key general protection modules (Intelligence, White-list, Geo/IP/Region Blocking, Rate Limiting, and Custom Rules) with its four major scenario protection modules (DDoS Protection, Bot Management, API Security, and WAF).
This integration allows general protection functions, which were previously only available for specific scenarios, to be applied across all scenarios. Additionally, it enhances collaborative analysis and intelligence sharing between different scenarios, making the protection more multidimensional. As a result, the platform achieves more comprehensive and advanced Web Application and API Protection.
Specifically, the following highlights of enhanced protection capabilities are particularly noteworthy:
- Automated L3/4 DDoS Protection
- Advanced Access Control Based on IP/Geo/Custom Rule
- More Flexible Rate Limiting Thresholds Settings
- Built-in Rules for L7 DDoS Protection with a Single Click
- Dynamically update the baseline via self-learning business traffic and attack features for L7 DDoS Protection
- SlowLoris Attack Mitigation
- Intelligent Analysis for WAF
- 900+ WAF Threat Patterns
- WAF Rulesets & Recommendation Exception
- Advanced Detection (Intelligent Risk Detection) for APBs
- Browser Bot Detection (Upgraded Bot Feature Verification)Typically for Replay Attack
- API Discovery
Why You Need Cloud Security 2.0?
If the aforementioned enhancements in protection capabilities are not straightforward enough, let’s interpret how CDNetworks Cloud Security 2.0 operates in real-world attack and defense scenarios from an enterprise perspective.
-
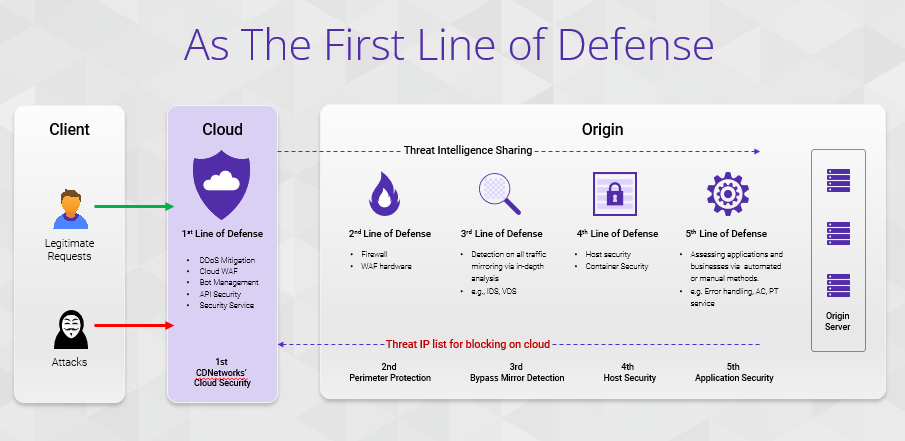
The First Line of Defense
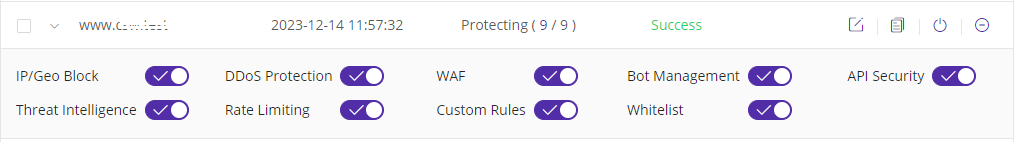
All cloud security services provided by CDNetworks (DDoS Protection, Cloud WAF, Bot Management, API Security, and complementary Security Services) act as the first solid line of defense in attack and defense scenarios. All requests from legitimate users and malicious users, such as hackers, will first pass through this CDNetworks cloud security defense before reaching the enterprise’s origin server. Within this defense line, the aforementioned 5 general protection modules and 4 scenario-specific protection modules will play a role in the following layers of protection to screen and protect online business requests. Enterprises can enable protection for different website domains with a single click, without complex configurations.
-
Closed-loop Risk Management
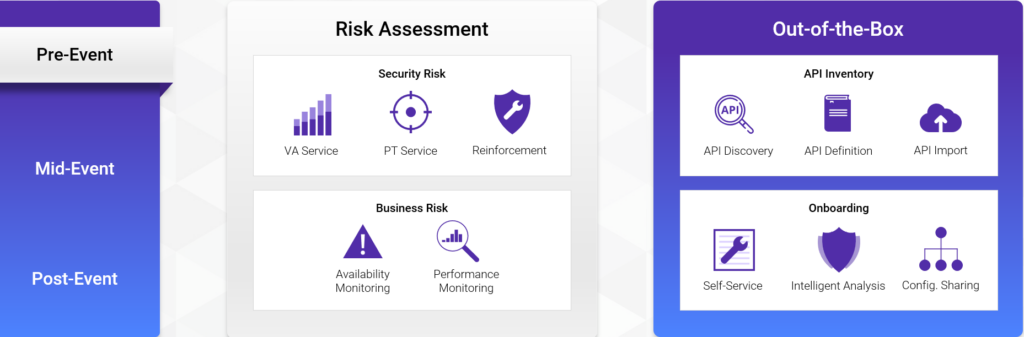
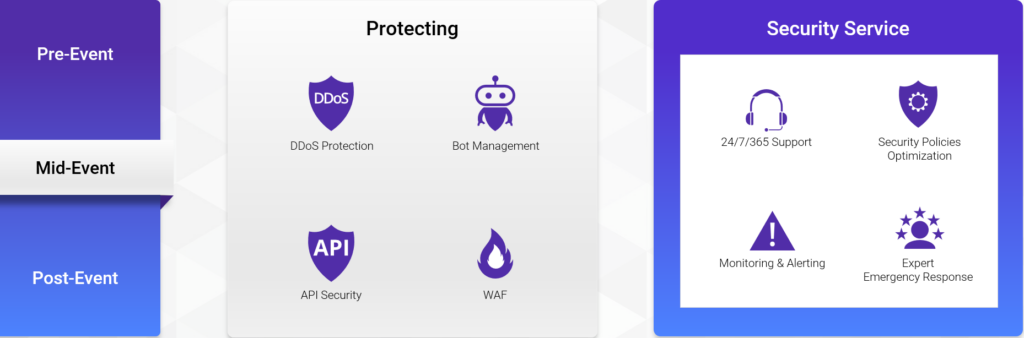
For enterprises, a complete attack can be divided into three phases: before, during, and after the attack. Only through timely and effective prevention, support, and optimization in these three phases can enterprises minimize losses from cyber-attacks.
Before the attack, CDNetworks uses risk assessment as a starting point to provide enterprises with preventive measures such as vulnerability scanning, penetration testing, and system hardening. These measures help enterprises identify and improve internal system issues early, thereby reducing the attack surface as much as possible. CDNetworks also offers a comprehensive set of self-inspection and sorting tools for unknown assets like APIs, which are easily exploited by attackers, to help enterprises standardize internal operation. Additionally, CDNetworks continuously monitors the operational status and availability of the enterprise’s business to ensure a swift response as soon as an attack is launched.
During the attack, in addition to the platform’s inherent powerful protection capabilities, CDNetworks’ security services also provide robust support for enterprises during attack incidents. Through close communication and intervention, enterprises can seek help from CDNetworks according to their preferred cooperation model. This comprehensive security service system helps enterprises minimize business losses caused by attacks as quickly as possible, playing a crucial role in protecting the enterprise’s reputation.
After the attack, enterprises can use the Security Posture Overview provided by CDNetworks to review the attack comprehensively, gaining a full understanding of the attack’s nature and improving their security posture accordingly. CDNetworks will analyze the attack and the enterprise’s related defense strategies to propose improvement measures. They will also meticulously help enterprises enhance their precise protection capabilities during future attacks, avoiding excessive false positives and false negatives that could further impact business.
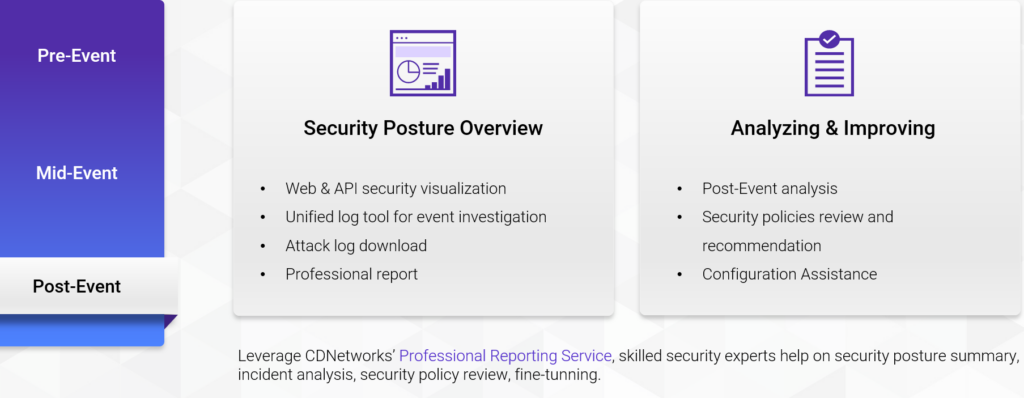
-
Intuitive UI and Consolidated Platform Capabilities
In the newly launched CDNetworks Cloud Security 2.0, CDNetworks has significantly improved the interactive experience of the Console Portal. Whether it’s enabling protection with a single click, intelligent management, bulk configuration for multiple domains, virtual patches for 0-day vulnerabilities, or numerous built-in rule sets summarized from security operation experience, the functional enhancements are substantial. Additionally, the Dashboard page provides unified monitoring and visual reports of different attack dimensions and web traffic. Standard API interfaces are also provided to facilitate customers in integrating their own origin protection systems for unified management, making the overall platform interaction very user-friendly.
Overall, the platform not only provides effective protection from L3 to L7 layers but also helps enterprises handle traffic surges during attacks or peak business periods through Elastic Scaling, ensuring smooth business operations. Notably, to address the complex needs of many enterprises in the multi-cloud era, CDNetworks Cloud Security 2.0 also supports multi-cloud management for various Web Services.
According to preliminary assessments, with its user-friendly interface, powerful adaptive security protection, and the operational management support it provides, enterprises can save approximately 50% of their daily security operation costs. All of this awaits you to apply for free trial and experience it immediately.
In conclusion, Cloud Security 2.0 offers a comprehensive and powerful solution to today’s security concerns. This consolidated security platform is an essential upgrade for your businesses, providing a seamless and effortless way to maintain security. Don’t wait until it’s too late – enable the upgraded WAAP solution along with Cloud Security 2.0 and give your business the protection it deserves.


