Over the last month, there have been successive reports of attacks by LockBit ransomware on various entities, from large commercial banks to aviation giants to Canadian government agencies. These attacks have led to serious consequences such as business interruption and data leakage, attracting widespread attention. So today, we are going to discuss LockBit Ransomware and give you a quick guide on how to avoid becoming its next victim.
Deep Dive into LockBit Ransomware
LockBit is one of the most active cybercrime organizations globally, primarily targeting businesses and institutions with high-value data or those that cannot afford business interruptions. It encrypts victims’ data and demands hefty ransoms. Victims span across numerous industries, including finance, manufacturing, energy, government, healthcare, education, and operators.
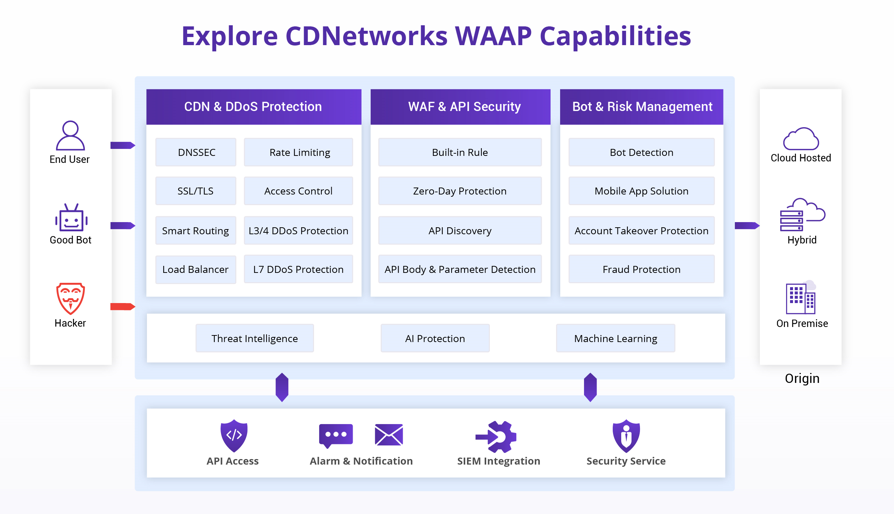
The LockBit ransomware presents widespread threats, and the recent instances of it exploiting system vulnerabilities are particularly alarming. It’s highly recommended that organizations which haven’t implemented any protective measures yet, to promptly utilize the CDNetworks WAAP solution. This will offer your organization’s web applications and API protection a comprehensive protection and help in preventing potential losses.
Exploring the Mechanisms of LockBit Ransomware Infections
According to monitoring by CDNetworks’ security expert team, LockBit is exploiting several publicly known 1-day and N-day vulnerabilities on a large scale across the entire network., and carry out ransom attacks. The exploited vulnerabilities include sensitive information leakage vulnerabilities in NetScaler ADC and NetScaler Gateway (CVE-2023-4966), as well as vulnerabilities in commonly used office and OA software.
After exploiting vulnerabilities to gain WebShell permissions, the attacker can directly run ransomware to encrypt user files to demand ransom. This ransomware is effective on both Linux and Windows systems, and the encrypted files have the extension “.locked1”.
The suspicious Locked1 C2 Addresses are 80.92.205.181 and 172.245.16.125.
A Guide to Protecting Your System from LockBit Ransomware
Prevention is the best defense against LockBit ransomware. At this moment, organizations should take actions to fix the relevant vulnerabilities as soon as possible. Following this, CDNetworks WAAP solution is a good choice to offer application protection against new threats using intelligent back-end monitoring that detects and blocks unwanted behaviors.
In the event of detecting 0-Day vulnerabilities, CDNetworks WAAP solution sends an “efficient patch” of WAF rules to the entire platform synchronously to fix the 0-day vulnerabilities. In doing so, a “Network-wide Synchronization” protection system is activated, consequently preventing any 0-day vulnerabilities from evolving into 1-day or N-day vulnerabilities due to delayed management and ultimately becoming vulnerable to ransomware attacks.
And CDNetworks WAAP Solution can effectively defend against attacks exploiting vulnerabilities in common third-party components (See Related Trends in CDNetworks’ WAAP Report 2022). It can block high-risk attack behaviors, such as command injection and WebShell uploading, in real-time. These behaviors are attempted by attackers who exploit known or unknown vulnerabilities, thereby preventing the possibility of attackers gaining server permissions. This fundamentally eliminates the risk of criminal organizations operating ransomware and carrying out subsequent attacks.
How to Respond if You’re Infected by LockBit Ransomware
If you suspect your organization has been infected by LockBit, please contact our security expert team to assist you in analyzing the source, and take emergency response measures.
Understanding and defending against LockBit ransomware is crucial in today’s digital world. But please remember that prevention is still the best defense against LockBit ransomware.
Please click here to apply for a free trial of CDNetworks’ WAAP solution for next-time ransomware attacks before it’s too late.


